A virtual private network, or VPN, is an essential tool for staying safe and secure online. Connecting to a VPN can keep your browsing private and away from prying eyes, making it more difficult to track your online activity.
When shopping for a new VPN or researching how to optimize your service you’ll likely run into a head-spinning amount of technical jargon. Encryption this and protocol that. Even reading VPN reviews can seem like a foreign language at times.
So to help you make sense of it all, we’ve compiled a list of the top terms and VPN features that everyone should know. Understanding the following terms can help you more confidently navigate the VPN environment and better understand what a VPN provider offers.
Further reading: The best VPN services
Custom DNS
DNS, or Domain Name System, is a way for web addresses to be translated into numeric IP addresses. Normally, a VPN manages DNS independently without guidance from the user. However, custom DNS is an advanced feature that allows users to specify a DNS server while connected to the VPN.
There are a number of reasons why one would want to change their DNS settings, but some of the most common are to increase browsing speeds and bypass website or ISP censorship restrictions.
The use-cases for a custom DNS are very specific and the average VPN user won’t likely benefit greatly from messing around with the DNS settings. However, if you’re a tech-savvy user or someone who likes to tinker, then you may find certain benefits to customizing your DNS while using a VPN.
Dedicated IP
Surfshark VPN offers an optional add-on dedicated IP address feature.
Surfshark
A dedicated IP is a premium add-on feature that many VPN services offer to users. If you opt for a dedicated IP, then the VPN will provide you with a static IP address that is unique to you, but still hides your true home IP address while connected.
While it will cost extra money, a dedicated IP can have impactful upsides. It can more easily unblock streaming services as it won’t likely be previously blacklisted for being a VPN server. It will also have more success bypassing many extra verifications, such as CAPTCHAS, when logging in to your accounts as you won’t be mistaken for a bot.
DNS leak
As mentioned above, the Domain Name System, or DNS, translates a web address into a numeric IP addresses. This process is usually done by your internet service provider (ISP), meaning that they’ll be privy to every website you visit.
When you use a VPN, the DNS translation process is done via the VPN instead of your ISP. This is one of the ways that a VPN can help keep your online activities private. However, while connected to a VPN there is a chance that your DNS can leak and expose your web browsing and IP address.
This often occurs with an improperly configured VPN or if the VPN connection fails. During our review process here at PCWorld, we rigorously test every VPN service for any DNS leaks.
Encryption
Sam Singleton
This is the process of securely concealing data by converting it into indecipherable digital code. Once the encrypted data reaches its destination, a cipher will then be used to decrypt the data. Most data sent over the internet is not encrypted and thus vulnerable to cyber threats and prying eyes.
A VPN not only obfuscates your true connection but also encrypts your data while traveling between servers. There are many different types of encryption, but VPNs will most often use AES-256, which is the industry standard due to its “military-grade” encryption strength.
Five Eyes
Five Eyes is an international signal-sharing intelligence agreement. The members include the U.S., Canada, UK, Australia, and New Zealand. There are also other international agreements such as Nine Eyes and 14 Eyes.
If a VPN is headquartered in one of these countries, it may be subject to data-sharing laws that could compromise a user’s privacy. Therefore, if you’re concerned with your anonymity while using a VPN, it’s a good idea to look for a VPN located in a country outside of the jurisdiction of these alliances.
Geoblocking
Sam Singleton
Geoblocking is the act of restricting or limiting access to online content based on a user’s home IP address. This most often comes in the form of a streaming platform, such as Netflix or Amazon Prime, blocking content in another country.
A VPN is one of the best ways to get around these restrictions so you can always access the content you’ve paid for, no matter what country you find yourself in. A VPN’s ability to access this geoblocked content is an important factor to consider when looking for a good VPN service.
Further reading: The best VPN for streaming Netflix
Kill switch
Often included with VPNs, a kill switch will cut off your internet access should you lose connection to your VPN for any reason. This will ultimately prevent any of your data or internet traffic from being exposed and visible to others should the connection unexpectedly drop. It’s a must-have feature in any good VPN.
Logs
Various logs and data records are kept about user activity either from an ISP or VPN service. In general, there are two types of logs kept by VPNs: connection logs and usage logs.
The first, connection logs, are typically only kept for shorter periods of time and allow VPNs to monitor and assess server load and maintenance requirements. They are generally anonymous and only contain data about connection type, duration of connection, and what device was used to connect with.
Usage logs are the important bit that users should be concerned about. Most reputable VPNs claim to abide by strict “no-log” policies, which actually means they keep no usage logs. This type of data can contain personally identifiable information such as a user’s home IP address, and detailed information about their web traffic. When choosing a VPN make sure to look for their no-log policy as well as any independent security audits they may have undergone to confirm this claim.
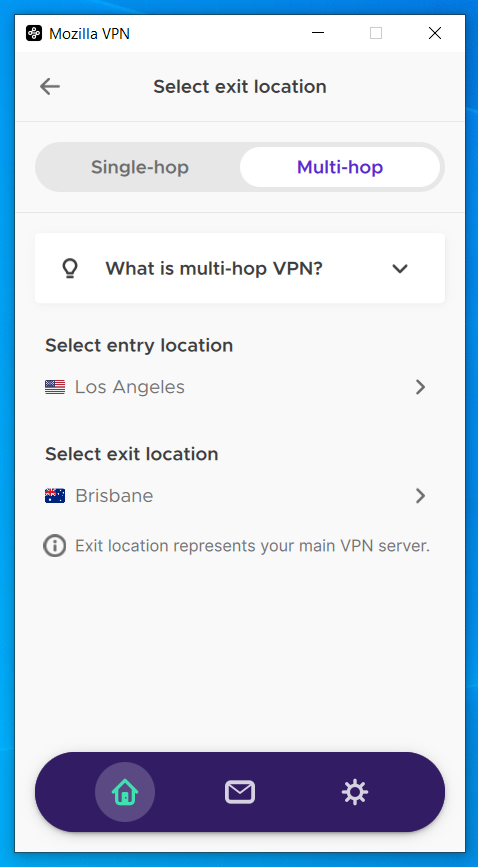
Multi-hop
Sam Singleton
Multi-hop is a rather new feature for most VPN services and you’ll still find many that don’t even offer it. This feature allows users to route their traffic through two or more VPN servers rather than just the standard one. The goal here is to further obfuscate the user’s true IP address and add an extra layer of security to the VPN connection.
Each successive VPN server you route through will likely slow down your connection speeds even further though. That makes multi-hop an excellent option for basic browsing activities, but may hinder your ability to game or stream HD videos while connected.
Further reading: How to test your VPN speed
Onion over VPN
The Tor (The Onion Router) network allows users to safely and privately browse the internet by directing web traffic through several routers, or nodes, making it difficult to track and identify their activities.
Using Onion over VPN simply means that you first connect to a VPN server before you begin using the Tor browser. In doing so, you add an extra layer of security and anonymization to your connection. This is a great security measure as it can protect you from any potential threats from compromised or dubious servers within the Tor network.
P2P (Peer-to-Peer)
This refers to a file-sharing network in which two or more parties can exchange files with one another, rather than via a centralized server. The most common form of P2P sharing is torrenting, which is done via the BitTorrent network.
Be aware, though, that depending on the types of files you’re torrenting, you may be violating an ISP’s terms of usage and could have your internet connection throttled or even terminated. Many VPNs nowadays support P2P sharing, so it’s highly recommended that you use a VPN at all times while torrenting.
Server count/server spread
If you hear about a VPN’s server count or server spread, this just means the number and location of the servers in a VPN’s network. This can be anywhere from a few hundred servers to thousands spread all across the world. A larger server count is often, but not always, a strong indication of a good VPN service.
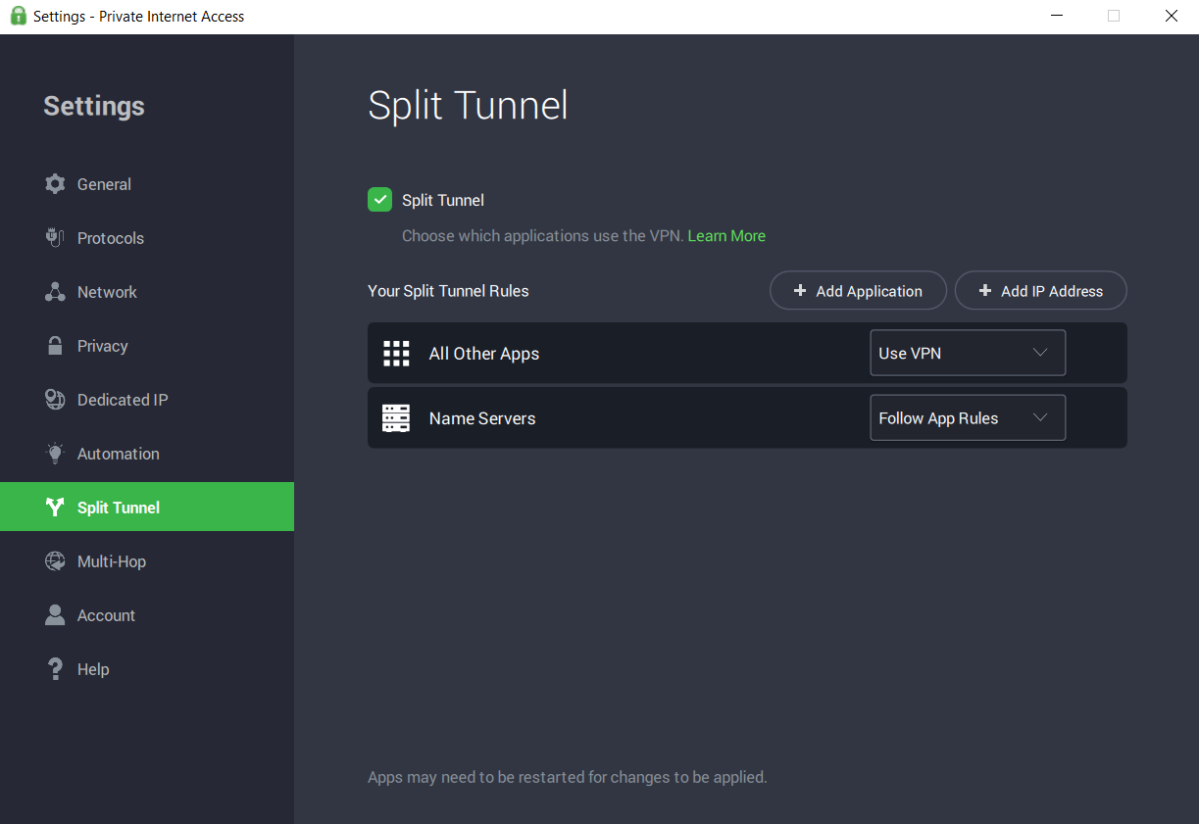
Split-tunneling
Sam Singleton
Split-tunneling is a nifty VPN feature that allows you to create two VPN tunnels at the same time. This can be used to allow certain apps or programs to run through a VPN server while others stay connected to their home ISP.
There are a few common ways to utilize this feature. The first is to protect your internet activity while browsing the web with one tunnel while the other tunnel is used to protect apps on your phone or computer.
The second common way to take advantage of split-tunneling is by running your internet browser traffic through a VPN while you leave your online games connected to your regular ISP. This way you can browse the web safely while keeping the maximum connection speed of your home internet.
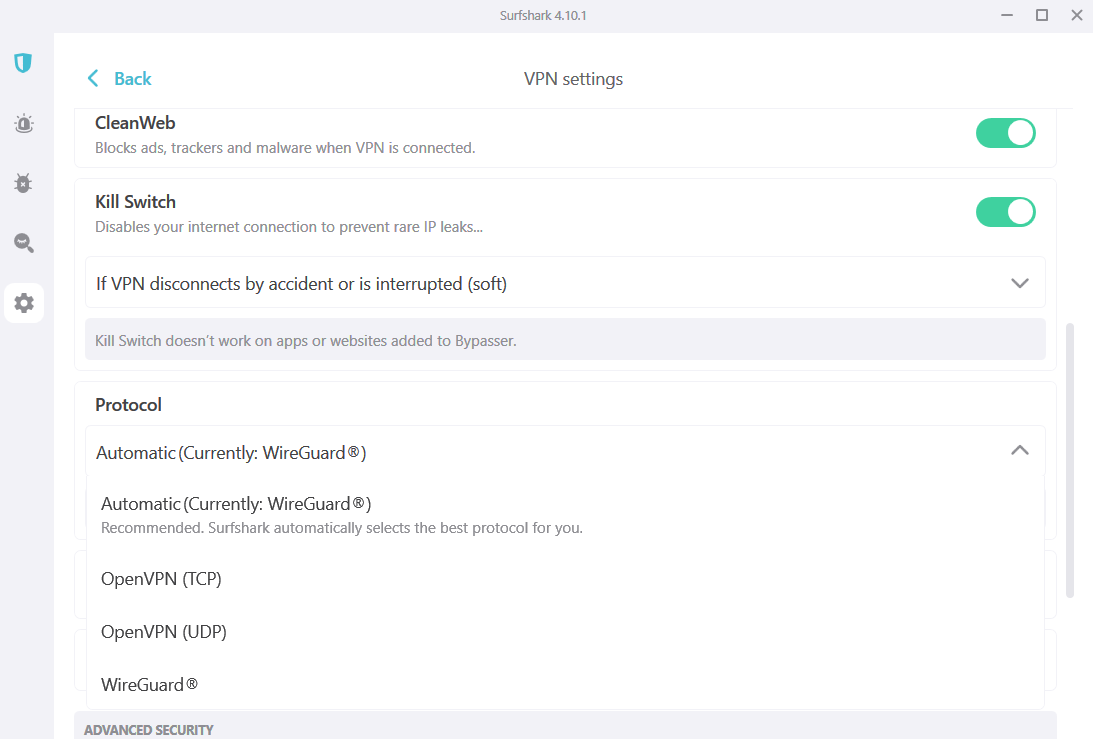
VPN protocol
Sam Singleton
A VPN protocol is a set of rules that govern how data is encrypted and sent between your device and a VPN’s server. Different protocols focus on different features such as high speeds, robust security encryption, or network stability. However, no protocol is perfect and each has tradeoffs.
There are numerous protocols on offer nowadays, but the most common VPN protocols are OpenVPN, IPsec/IKEv2, and WireGuard. The OpenVPN protocol is a great option for security and stability. IPsec/IKEv2 is decently fast and very secure, but is mainly used to keep devices on the move secure as the VPN connection won’t drop when switching between Wi-Fi and mobile data. WireGuard is the latest protocol and it’s extremely fast and secure and has the added benefit of being open source.
At PCWorld we recommend that users opt for either WireGuard or OpenVPN as these provide the best mixture of speed and security.



