Network security is not just for IT professionals. Even home users need to keep their networks secure to prevent unauthorized people from, for example, hogging their broadband, installing malware that turns connected devices into robots in botnets, and spying on what you and your family are doing.
In the past, the internal network was often considered safe and protection against threats from the internet was the most important thing, but today security experts recommend using encrypted connections as much as possible even within the local network.
It may seem complicated, but with basic knowledge and the right settings in your router, you’ll go a long way.
Further reading: 4 preventative steps to avoid a home networking disaster
Network security starts with the right router settings
The security of your network is based on the fact that only you, your family members, and visitors should have access to it, while everyone else is excluded. A basic requirement for this is that your router is set up so that only you can change settings, and your wireless network so that no one can connect without getting the password from you.
Change the password on both the router login and the Wi-Fi network
Before you do anything else, make sure you’ve changed the password for both the router’s admin panel and the Wi-Fi network. Most Wi-Fi routers today have randomized passwords, but several manufacturers have been found to have insecure algorithms and I don’t recommend trusting them. Also, it’s all too easy to quickly take a picture of the underside of the router where the default password is usually printed. For the Wi-Fi password, three to four random words without any numbers or special characters is fine, as it’s much easier to type by hand than an incomprehensible string of characters.
Switch off unnecessary features
Many routers, especially older ones, have two unsafe features enabled by default that you should turn off if you’re not sure you need them: UPnP and WPS. The former may be needed by some programs that want to receive incoming traffic, but it’s better to have it turned off and turn it on if you later discover you need it than to leave it on just in case. WPS is a way to quickly connect a product that doesn’t have simple input like a keyboard to the wireless network, but it’s an insecure technology and not needed today. Modern gadgets use QR codes, mobile apps, and other methods to securely connect them to the network.
Switch off remote login
Thankfully, logging in to the router’s admin panel from the internet is normally turned off by default, but it’s still best to check and turn it off if it’s still on.
Better DNS than your ISP’s
If you don’t change any settings, your router will normally send all domain name queries to your ISP’s DNS server, but there are better options. You can either choose one of the big, well-known regular DNS servers, like Cloudflare’s 1.1.1.1, or encrypted DNS if your router supports it. With encrypted DNS, your ISP can’t see what sites you and all your devices are connecting to.
MAC filters are useless
When home networking was new, it was common to advise users to limit access to the network to selected MAC addresses (hardware addresses). Since it’s very easy to copy another device’s MAC address, this doesn’t actually increase security and is mostly a hassle as you have to manually authorize each new device. If you have MAC Address Filter running, switch it off and leave it off.
Asus
Use https for router settings
If someone has somehow gained access to your network, they can monitor all traffic. If you connect to the router’s admin panel and log in with an unencrypted connection (http://), the hacker will get the login details. Therefore, it is always best to connect to the router encrypted.
Many modern routers automatically have a self-generated SSL/TLS certificate and you can connect by simply adding https:// in front of the address, for example https://www.asusrouter.com:8443 on Asus routers. Unfortunately, not all manufacturers have enabled support for https, and if you care a lot about security, it might be worth considering upgrading if your current router doesn’t have the option to even enable it in the settings.
On the most sophisticated routers, you can also activate a certificate issued by the free service Let’s Encrypt. This requires you to have a domain name, either one you’ve bought or one obtained through a dynamic DNS service. Asus is a role model here, with built-in support for several services, including its own that gives the network a domain of the form yournetworkname.asuscomm.com. Then you can enable the Let’s Encrypt feature, which automatically obtains a certificate, and then access the router settings via https://yournetworkname.asuscomm.com (instructions here).
Having a domain name and certificate does not mean that anyone can try to log in from the internet — normally you should have the router set to only accept connections to the admin panel over the local network.
If you have a NAS device or any other server on the network with a web-based admin interface, you should also connect to it using https. Some manufacturers, like Asus, have thought about this and made it easy. For example, Synology has instructions here.
TP-Link
Keep your router and gadgets up to date
Almost as important as not having “password” as a password is keeping both the router and connected devices up to date. New security flaws are discovered all the time and if you don’t update, you leave your devices open to attack.
It is best that as many devices as possible have automatic system updates, but for those who do not have such a function, it can be a good idea to set a reminder or recurring calendar activity to check for updates, for example once a month.
Firewall – in the router and in each computer
A firewall, in the context of networking, is a program that controls all network traffic to and from a device and allows or blocks traffic based on pre-set rules. Windows, Mac OS, and most Unix and Linux variants have a built-in firewall. In Windows, it is included in Windows Security, under Firewall and Network Protection.
There aren’t many settings here, but at the bottom you’ll find a list of shortcuts to additional features. Allow an app on the firewall is a tool to add exceptions for individual programs or change existing rules. Select Advanced Settings to open the full firewall controls, which are located in an old-fashioned interface such as Device Manager.
In the latest versions of Windows, the firewall is automatically on and you rarely need to make any settings, but the same is not true of all routers. Check your own router by logging into the admin panel and looking for a firewall or firewall. Search online if you can’t find it. Activate the firewall.
A tip if you have a Pi-hole (see below) is to block traffic on port 53 (DNS) to all addresses except Pi-holes. This will prevent devices from using other, unsecured DNS servers. It can be circumvented with encrypted DNS, but stopping it is much trickier.
Foundry
Pi-hole stops advertising and tracking for all devices
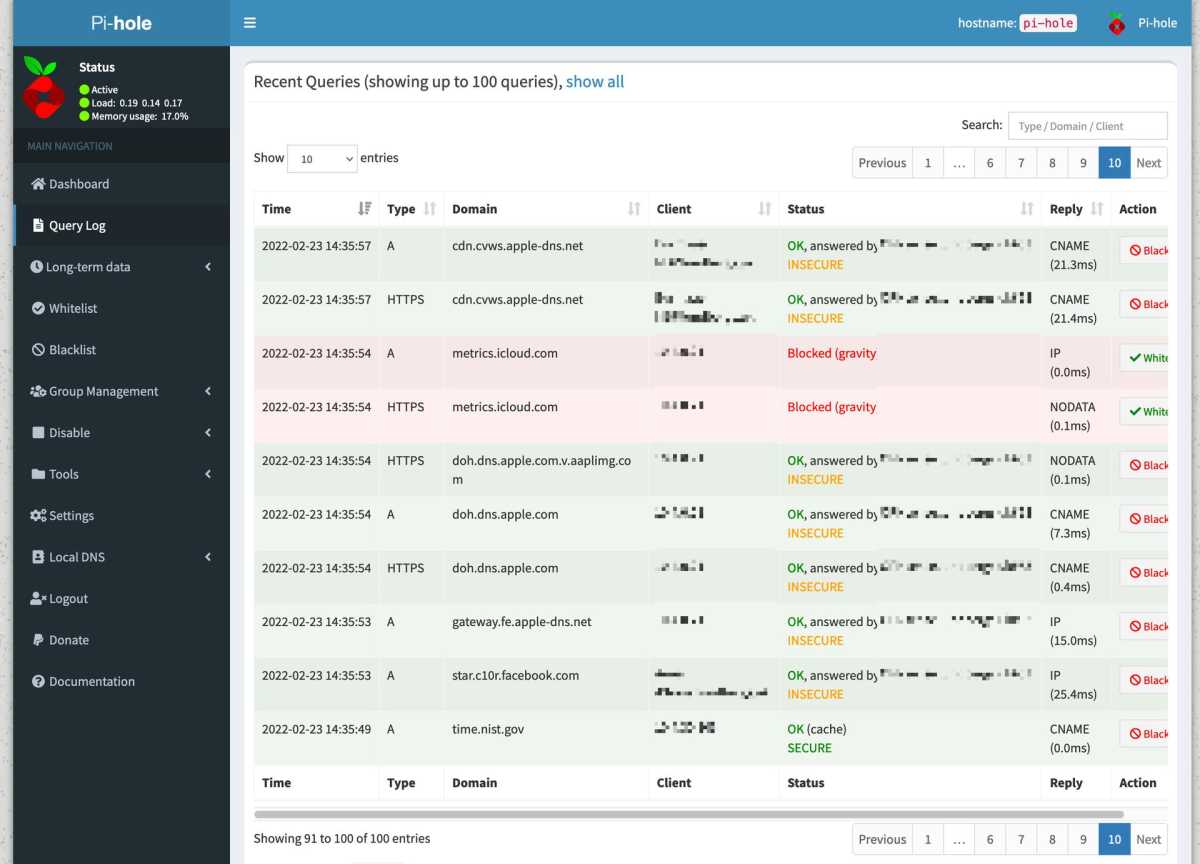
If you want to take your resistance to ad tracking to the next level, take a look at Pi-hole, a DNS server with filtering capabilities that you can run on a Raspberry Pi, for example (hence the name). With a Pi-hole on your network and smart settings on your router, you can ensure that all devices on your network, including TVs and smart home gadgets, are protected from tracking.
Pi-hole uses imported filter lists and blocks connections by not responding with an IP address when a device tries to look up a domain name. If a website is not working properly, it may be because a domain it uses is on your filter lists. You can then whitelist that domain to allow it regardless of what the filter lists say.
Use guest networks if your router has them
Many routers have a clever feature called a guest network. This is a separate wireless network with its own password that you can give to temporary visitors, allowing them to access the internet. The guest network does not have access to the local network, so those connected to it cannot try to connect to your other devices or to other guests.
Check your router’s settings to see if it supports a guest network and enable it if it’s not already running. As with the regular Wi-Fi network, you should choose a secure password so that only the guests you actually want to connect can.
Make a separate network for connected gadgets
Behind the scenes, guest networks use a technology called VLAN to create separate virtual networks, and on some advanced routers you can set up additional such networks yourself and even create separate Wi-Fi networks that belong to a VLAN. Devices on a VLAN have different IP addresses — if your regular network has addresses between 192.168.0.1 and 192.168.0.254, you can set up a VLAN to use 192.168.100.1-192.168.100.254, for example.
A great use for a home VLAN is as a standalone smart home network. Connected gadgets like video doorbells, lights, and refrigerators hardly need to communicate directly with your computer and mobile phone.
This is not included in basic consumer routers and is quite complicated. If you have installed alternative software in your router, such as OpenWRT or Tomato, you can search for guides. A simpler option is to simply connect the smart gadgets to the guest network. A disadvantage of this is that gadgets that want to communicate with, for example, an ironing app on your mobile phone via the local network may fail.
Further reading: Why you should always set up guest Wi-Fi at home
Keep track of connected devices
It can be a good idea to check from time to time what is connected to the network, so that no unauthorized devices have entered after all. Some routers have a function in the admin panel to list all connected devices (usually called something like “connected devices”). If your router doesn’t have a list, you can use a program to scan the network for connected gadgets.
Unfortunately, some routers have the habit of only listing devices that have automatically received their IP address via the DHCP protocol and not devices that have a fixed address, so using one of these programs can still be a good idea.
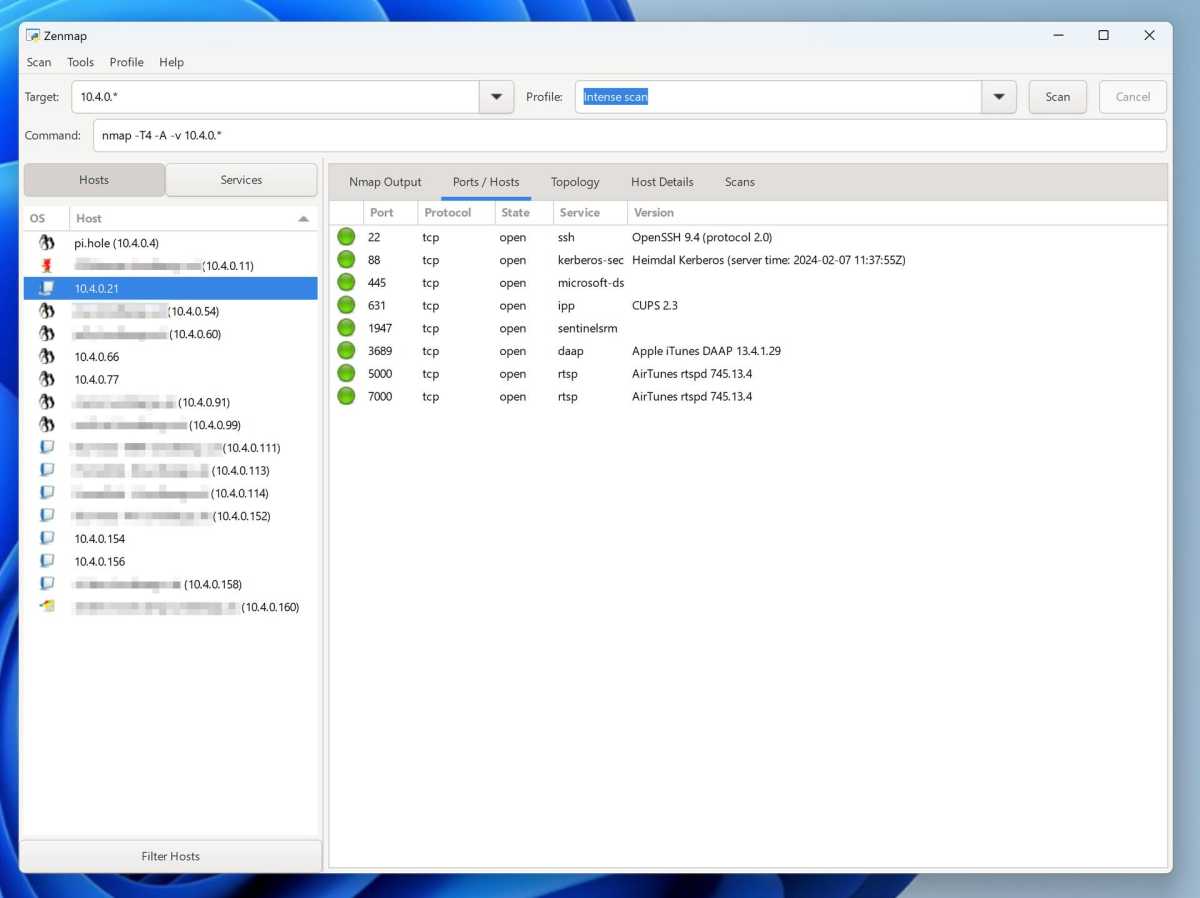
For the most complete scan of the network, I recommend the Nmap program. It’s a bit more complicated than other programs, but can find devices that don’t respond to ping, for example. The Windows version comes with a graphical interface called Zenmap, which still makes it fairly simple.
Foundry
Once the program is running, all you have to do is fill in the address range you want to search through. For example, it could be 192.168.0.* for addresses between 192.168.0.1 and 192.168.0.254. Then click Scan and wait for the results. In the column on the left you will see the different devices on the network and if you click on Host Details you can see details such as what operating system the highlighted device is running.
If you find something you don’t recognize, it doesn’t necessarily mean that someone has accessed the network or hacked you. Most likely, it’s some gadget you haven’t thought of. Do you have any smart home gadgets, connected appliances, smart speakers, modern TVs, or video game consoles? It’s not uncommon to have dozens of devices on the network.
If you find something that you’re absolutely sure shouldn’t be there, change the password on the Wi-Fi network and restart the router so that all devices have to reconnect. It can be a bit of a hassle to change passwords on some devices, but it’s better than having someone unknown on the network.
Further reading: 6 big home Wi-Fi mistakes, and how to fix them
This article was translated from Swedish to English and originally appeared on pcforalla.se.



